EU Regulation No 910/2014 (eIDAS) addresses the creation of remote electronic signatures using electronic signature creation data that is managed remotely by a third-party trust service provider (TSP) working on behalf of the signee.
These TSPs are required to use specific security procedures, both managed and administrative, to ensure that their electronic signature creation environment is secure, reliable, and under the signatory’s sole control.
eIDAS requires that qualified electronic signature creation devices (QSCDs) are used in creating qualified electronic signatures.
High-Level Process of Qualified Electronic Signing
eIDAS created a set of standards that ensure that official or legally sensitive digital business across EU member state borders can be securely conducted – based on digital identities. The qualified electronic signature is one of these standards. A qualified electronic signature (QES) carries the same legal weight as a written signature and may even be considered more secure.

In simple terms, a qualified electronic signature is an advanced electronic signature that has a qualified digital certificate attached to it.
But there is more to creating a qualified electronic signature than just attaching a qualified certificate. The QSCD must use certified hardware and software to ensure that the signatory maintains in control of his/her private/signing key.
To be considered at a qualified level, the electronic signature must meet three requirements:
- The signature must be uniquely identified and linked to its signatory.
- The data that is used to create that signature must be under the signatory’s sole control and no one else.
- Tamper-proof protections must be in place to identify if tampering has taken place with the data that accompanies the signature since the signing of the message.
The Qualified Signature Creation Device in the Context of Remote Signing
A system that provides remote signature services must ensure that the signing party has sole control over their signing key(s) and that the key is used only for its intended purpose. A QSCD is only one component within the remote signing ecosystem.
Such a system comprises an unprotected local user and the TSP protected remote environment. The graphic, as shown below, illustrates the two environments:
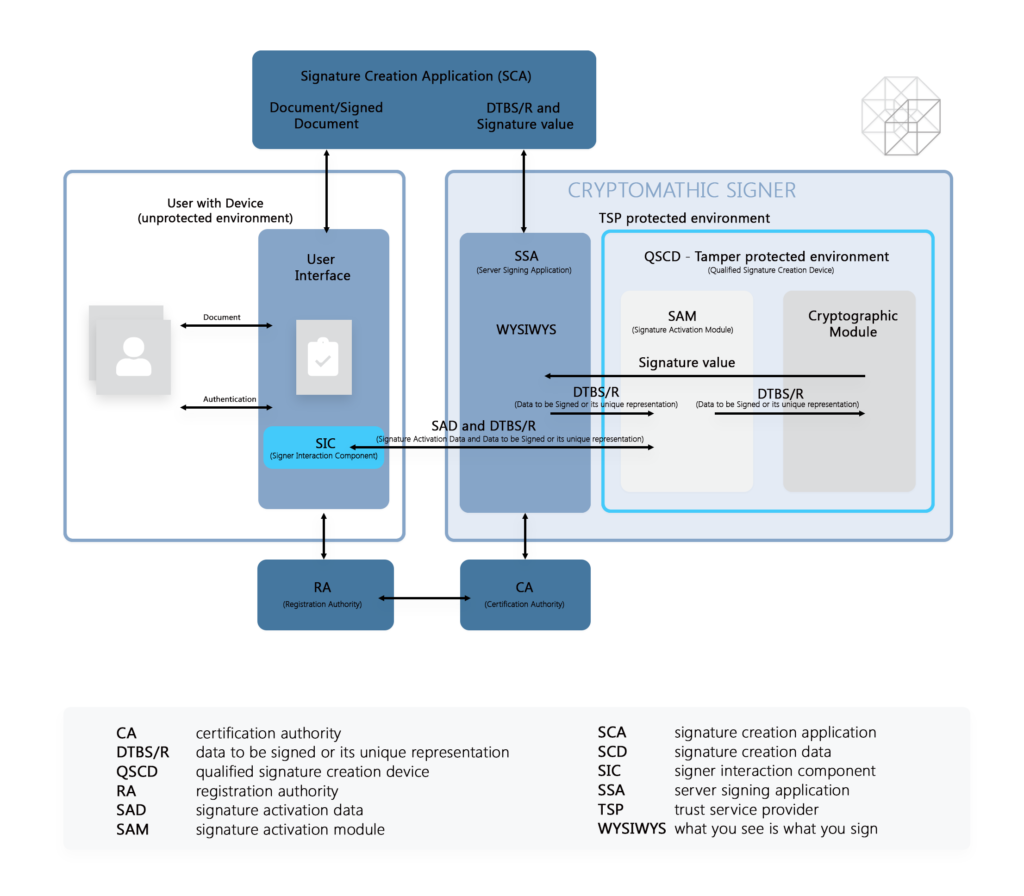
- The local environment contains the signee and a device that provides the user interface, such as smartphones, tablets, or laptops.
- Documents are displayed on the user interface for the signee.
- A signer interaction component (SIC) is used by the device to communicate with the server signing application (SSA).
- The SSA sends the SIC’s communication or from itself to the QSCD.
- The signature activation module (SAM) inside the QSCD receives the messages and may initiate further communications with the SSA to obtain additional relevant data.
- Once the SAM module has verified signature activation data (SAD), it then authorizes the Cryptographic Module’s signing key to produce a digital signature value.
- The digital signature value is sent to the SSA may also be sent to the signature creation application (SCA) or SIC.
- The SSA and the user interface act as supporting modules that display documents and forward communication messages.
The signing party resides in the local environment. It interacts with the remote environment through a connected device, such as a smartphone, tablet, or laptop. The interaction between the chosen device and Server Signing Application (SSA) is to allow the signee to use the SSA’s signing service. The signing operation is performed with a Signature Activation Protocol (SAP) that requires that Signature Activation Data (SAD) be available at the local environment. The SAD brings three elements together:
- Signer authentication
- Signing key
- Data to be signed (DTBS/R(s))
In ensuring that the signees/signing parties have sole control of their signing keys, the signature operation requires authorization. This is performed by a Signature Activation Module (SAM) that handles:
- One endpoint of SAP
- Verification of SAD
- Activation of the signing key residing in a Cryptographic Module
Both the SAM and the Cryptographic Module must be located in a tamper-protected environment. Verification of SAD means that the SAM verifies the binding that exists between the three SAD elements while ensuring that the signer is authenticated.
Signee authentication is one of the elements included under SAD. The SAM may carry out signee authentication in one of three ways:
- Directly, where the SAM verifies the signee’s authentication factor(s).
- Indirectly, where an external authentication service (e.g., one that is part of the TW4S or delegated party) verifies the signer’s authentication factor(s) and issues assertion that the signer has been authenticated. The SAM then verifies the assertion.
- Through a combination of two direct or indirect schemes, where the SAM performs part of the signer authentication directly, and another part is performed indirectly by the SAM.
When the SAM does not directly perform signee authentication, according to its environment, it must assume that part, if not all, the authentication has taken place and then rely on the assertion provided. This means that in the Protection Profile (PP) signer authentication, the signer has been authenticated using one of the three methods listed above.
With EN 419 241-2, the SAM module is the Protection Profile’s target of evaluation (TOE). Both the TOE and Cryptographic Module, certified according to EN 419 221-5, are required to obtain a QSCD.
Cryptomathic Signer incorporates a QSCD certified against EN 419 241 (Part 1 and 2)
QSCDs rely on both specific hardware and software to assure their secure functions. On the QSCD software front, Cryptomathic Signer has the strongest security credentials. It has undergone more security reviews than any other security solution of its type, including depth, coverage, functional tests, and independent testing.
Cryptomathic Signer is designed and certified to meet the highest standards required by:
- EN 419 241-1: Trustworthy Systems Supporting Server Signing Part 1, General System Security Requirements, CEN February 2018.
- EN 419 241-2: Trustworthy Systems Supporting Server Signing Part 2, Protection Profile for QSCD for Server Signing, CEN April 2019.
